Cybersecurity for Critical Infrastructure Demystified
05:08:2024
BY Andres Giraldo
In recent years, the cybersecurity of Critical Infrastructure has shifted from a niche concern to a national emergency prompted by the escalating number and severity of cyberattacks targeting essential services. As Jen Easterly, the director of Cybersecurity and Infrastructure Security Agency (CISA), mentioned during her opening statement before the House Select Committee, “This is a world where a major conflict halfway around the globe might well endanger the American people here at home through the disruption of our gas pipelines; the pollution of our water facilities; the severing of our telecommunications; the crippling of our transportation systems – all designed to incite chaos and panic across our country.”
This blog aims to answer why Critical Infrastructure remains vulnerable to cyber threats and how its cybersecurity needs to differ from traditional IT systems. We’ll also examine recent Critical Infrastructure attacks, recommend best practices to address them, and provide key resources for government agencies and private enterprise.
Critical Infrastructure: Its Importance in Our Daily Lives:
Critical infrastructure (CI) refers to the physical and electrical based systems essential to society’s functioning including electricity, water, transportation, telecommunications, chemical, and our food supply. It’s difficult to imagine how a cyberattack can affect all those services we rely on each day. But in recent years, we’ve seen glimpses of how these attacks affect the American people. The ransomware attack on Colonial Pipeline in May 2021 demonstrates how a cyberattack on CI can disrupt society by creating widespread fuel shortages and panic.
Challenges in CI Cybersecurity:
Traditional IT security prioritizes protecting data confidentiality and integrity, while CI cybersecurity prioritizes system availability and resilience. A disruption in critical sectors could result in dire consequences up to and including threat to human life. As FBI Director Christopher Wray testified during a Congressional full committee hearing in January 2024 regarding the China-backed hacking operation known as Volt Typhoon, “Cyber threats to our Critical Infrastructure represent real-world threats to our critical safety.”
Many CI systems rely on legacy technology not designed with modern cybersecurity threats in mind. These systems often cannot be updated or patched without significant disruptions, making them vulnerable to exploitation. A large number of devices used in Critical Infrastructure have been operational for decades and replacement components no longer exist. The risk of trying to patch some of these devices and potentially brick them is something to be considered.
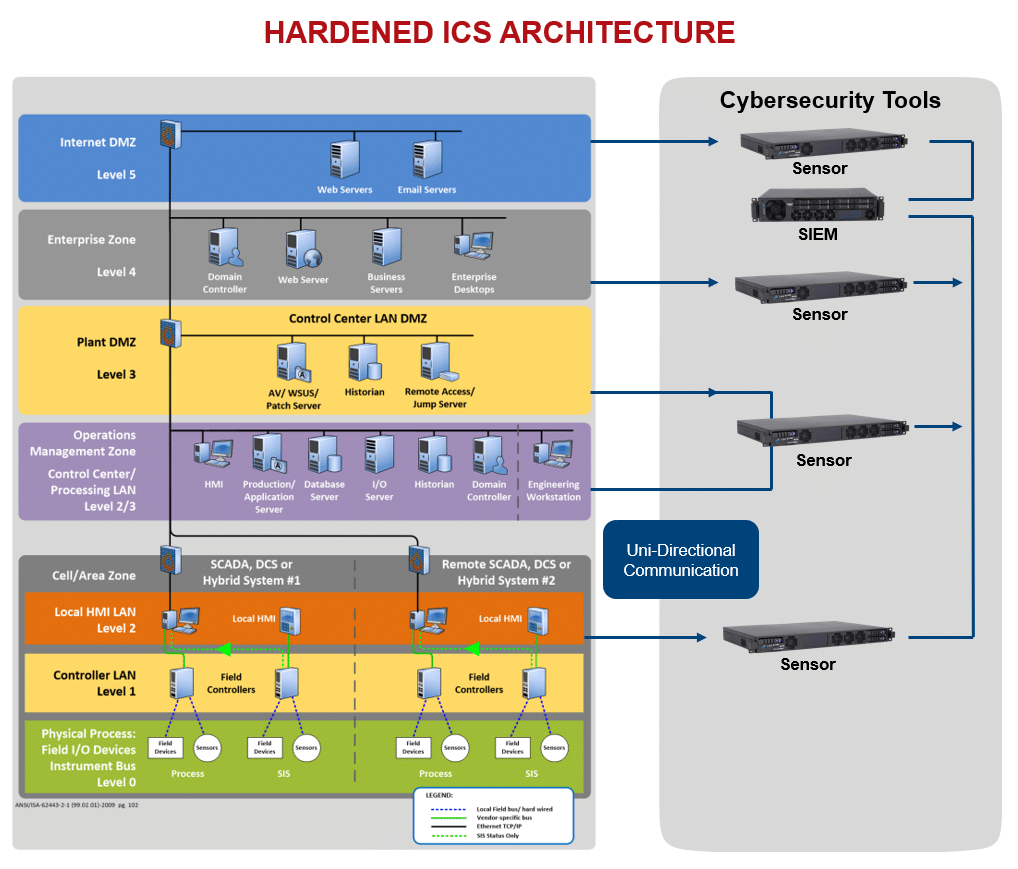
Critical Infrastructure Architecture & Terminology:

ICS Architecture
- OT (Operational Technology): Hardware and software that monitors or controls equipment, assets, or processes.
- ICS (Industrial Control Systems): Encompasses types of control systems, including SCADA and PLCs, used for industrial process automation.
- SCADA (Supervisory Control and Data Acquisition): Systems used to control dispersed assets, often found in utilities like electricity and water.
- PLC (Programmable Logic Controllers): Hardware that controls industrial operations and processes.
- HMI (Human-Machine Interface): A user interface or dashboard that connects a person to a machine, system, or device. HMIs are used by operators to monitor and control processes.
A History of Cyberattacks on CI:
Estonia Cyberattacks (2007)
Coordinated series of cyberattacks that targeted banks, ministries, media companies, and more. One of the first examples of coordinated cyber operations used to target an entire nation’s infrastructure.
Stuxnet (2010)
Targeted PLCs designated to automate electromechanical processes at nuclear facilities. This worm caused fast-spinning centrifuges to tear themselves apart.
Saudi Aramco Shamoon Attack (2012)
Attack on a large oil company that destroyed over 30,000 disk drives on devices throughout the network. This disrupted operations and increased oil prices throughout the world.
Ukraine Power Grid Attack (2015)
Attackers employed malware to gain control of the power distribution stations across various regions in Ukraine. This attack led to power outages affecting approximately 230,000 people. A multifaceted attack, it not only affected direct control of the systems, it also flooded telecommunications and hampered repair coordination.
U.S Water Utility Hack (2016)
Hackers infiltrated a water utility’s control system and changed the levels of chemicals being used to treat municipal tap water. Through SQL injection and phishing, attackers managed to exploit a control system connected to the Internet. This control system regulated programable logic controllers (PLCs) that administered the flow of chemicals used to treat tap water. Luckily the changes the attackers made did not work due to bugs in their SCADA code change. Similar cyberattacks continue to hit American water systems throughout the U.S.
Colonial Pipeline Attack (2021)
A ransomware attack used to disable computer systems managing the pipeline. This led to a shutdown that lasted several days and caused widespread fuel shortages and panic buying on the U.S. East Coast. It also highlighted vulnerabilities in its energy infrastructure to cyber threats.
Attacks on Critical Infrastructure provide risk of bad actors being able to turn off the lights for Americans, shut down cities, add chemicals to our water treatment, and cause massive loss of American lives. As CISA Director Jen Easterly testified, “We’ve seen Chinese cyber actors, including those known as Volt Typhoon, burrowing deep into our critical infrastructure to enable destructive attacks in the event of a major crisis or conflict.”
Best Practices & Hardening Critical Infrastructure:
As in traditional IT networks, the concept of segmentation becomes crucial to the overall defense in depth strategy for Critical Infrastructure. Using something like the Purdue Enterprise Reference Architecture (PERA) suggested by the Department of Homeland Security is a best practice for segmenting networks. This defines a demilitarized zone (DMZ) layer between the operational technology (OT) side (manufacturing, Control, Process) and IT side (Enterprise Network Services).
Strategic placement of network monitoring remains a critical aspect of defense. Continuous monitoring of your network helps detect unauthorized access, insider threats, and other malicious activities. Tools that provide visibility into network traffic also assist in identifying potential breaches. Being proactive in this way helps maintain your system’s integrity by ensuring that all operations proceed without interference and flag any anomalies so they can be investigated immediately. Understanding the importance of where to place monitors on a control system network affects it too. For example, devices like Human-Machine Interfaces (HMI) or Programmable Logic Controllers (PLC) can be sensitive to network probes and could result in operational disruptions. echnology aggregates and analyzes activity from many different resources across your entire IT infrastructure. It collects security data from network devices, servers, domain controllers, and more. By analyzing this data, SIEM can detect abnormal activities that may indicate a cyberattack or security threat. Real-time analysis and reporting provide an essential layer of intelligence, allowing security teams to respond to threats swiftly and effectively.
Following standards set by government agencies and industry bodies helps CI organizations adopt a minimum level of security practices. The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) standards are designed for power utility companies to follow and ensure the security of electric utility systems in North America. Other sectors may follow frameworks such as ISO 27001 or NIST guidelines. Compliance with these standards involves regular audits, detailed reporting, and remediation of any findings in security posture.
Consistent and ongoing training and awareness programs for employees should be standard. Human error often leads to the largest security threats for government agencies and large enterprise. Educating your associates on how to spot phishing attempts, the importance of strong passwords, and the proper handling of sensitive information never dims in importance.
Learn how SealingTech edge compute servers and our Cyber-Fly-Away Kits can help defend your Critical Infrastructure. Contact our team.
Related Articles
Perspectives & Post-Quantum Encryption: NATO Edge 24
In December, SealingTech Account Managers, Wade Saunders and Benjamin Young, traveled to NATO Edge 24 in Tampa, Florida—an annual forum for industry experts and peers to address current and future…
Disrupting Adversary Threats
As a Principal Solutions Architect for SealingTech and proud 20-year US Army Veteran specializing in defensive cyberspace operations, I take the threat of near-peer adversaries seriously. Near-peer adversaries are predatory…
AI Solutions that Support the Mission: TechNet Indo-Pac
Members of SealingTech’s team attended AFCEA’s TechNet Indo-Pac Conference in Honolulu, Hawaii in October. Its theme: “Free-Open-Secure” focused on the critical issues identified by regional military leaders to maintain and…
Could your news use a jolt?
Find out what’s happening across the cyber landscape every month with The Lightning Report.
Be privy to the latest trends and evolutions, along with strategies to safeguard your government agency or enterprise from cyber threats. Subscribe now.