CEO Cyber Session: Why SealingTech has Grown Exponentially for 10 Years
10:03:2022
Look back to May 29, 2022 – SealingTech just celebrated its first decade in business.
In those 10 years, SealingTech has been blessed with exponential growth due to the technological, cyber, software, hardware and integration solutions we have created and delivered to the US Department of Defense (DOD).
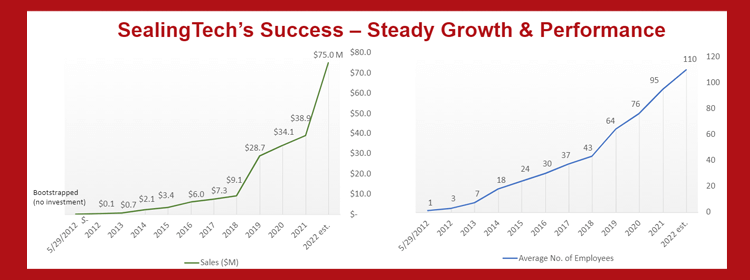
We’ve also had a few failures that have taught us some valuable lessons. But as a business, we’ve grown in revenue, team members, products and leadership experience. The table below provides a graphic representation of our 10-year revenue and staff growth.
In this and upcoming CEO Cyber Sessions blog posts, I’d like to touch on:
- How our 10-year growth happened
- What we learned
- What lessons may be of use to your business
SealingTech History
Our goal was to directly support defending our DOD customers and the American people from cybersecurity threats and attacks.
From 2012 to 2022, we’ve grown rapidly by creating products, services, and solutions to help solve the problems we saw in the DoD. During this growth, we were so busy getting the job done that we didn’t have a great deal of time to talk about our company, what we do or why we do it.
Why?
Because like many dynamic, entrepreneurial enterprises, we were so busy surviving and getting the job done we had little time to reflect on how it happened.
In other words, we spent so much time meeting the myriad demands of cybersecurity and completing projects we have not had time to reflect on our tasks, projects and programs and what they have accomplished to secure this nation’s cybersecurity.
But we realized that what we learned experientially has value to others, especially those who do not understand the cyber world we work in daily, and to those who want to do business or be a professional in the cyber domain.
So, with this and subsequent blog posts, I’m going to discuss:
- SealingTech’s business model
- What has led to some of our successes
- Lessons learned to defend against cyber-attacks
- Tips for how to apply and win contracts with DOD that may help others
Why SealingTech Exists
When talking about any company, it’s important to start with “Why do we exist?”
The answer to this question drives the decisions, philosophy, programs, projects, tasks, hiring, milestones and daily activities of our business, and is what keeps us rooted in our core mission.
A company that doesn’t have a firm answer to this question will tend to drift and struggle to succeed. I can tell you how we answer the question of why we exist.
Yes, SealingTech supports the DOD in keeping cyberspace safe, but that’s not really the complete answer for why we exist.
For that answer, it comes down to some core beliefs that transcend the DOD, our staff and our business. It’s what I would refer to as “Our calling.”
Personally, I believe in the core American values of:
- Democracy
- Freedom of all people
- Fair capitalism
The United States isn’t perfect, but unlike many other nations, we are a country that believes in:
- The fundamental rights of the people
- Fair and open commerce
- Anyone can come from nothing and build their way to success
We are the leaders of the free world. And our military helps ensure that we maintain our freedoms, peace, security and way of life.
In the past 10 years, the explosion of cyberspace and the critical role that computer systems, software and networks play in every aspect of our civilization has created new threats and challenges to our society.
SealingTech is a business platform where:
- We use our engineering and cybersecurity expertise to help ensure our military is dominant in cyberspace so they, in turn, can help keep our country and our freedoms safe.
- We exist to support our military and to make cyberspace a safe place for the United States and our allies.
To accomplish this critical mission, we had to define, learn and operate in cyberspace.
What is Cyberspace
Cyberspace is a warfighting domain.
The United States Joints Chiefs of Staff officially declared cyberspace the “fifth domain” of conflict in 2004. Cyberspace encompasses all areas in which computer programs operate in a globally connected environment.
Like the Air, Land, Sea and Space domains, it’s a medium for which damage can be caused and an adversary can cause interruption to the flow of a critical resource (in this case, information or command and control).
Cyberspace is a domain in which:
- Battles for dominance occurs in specified areas of operations.
- Supremacy of it can change the tide of a war, who wins and who loses.
Cyberspace operations are primarily used to:
- Perform intelligence operations
- Destroy critical infrastructure
- Take control of weapons systems
- Disrupt economies
- Conduct psychological operations on a mass population
The importance of cyberspace as a warfighting domain has caused countries around the world to pour billions of dollars into:
- offensive and defensive capability development, as well as
- training their forces to conduct cyberspace operations.
For SealingTech to accomplish our mission, we aligned our core beliefs in a strong market with a variety of problems that need to be solved.
This created the opportunity for SealingTech to be a successful business.
The Importance of the Cyber Mission
The United States has been blessed for 158 years without a conflict on our soil. Sadly, much of the world can’t say the same.
This era of geographic peace due to having a strong military and foreign policy is now over as cyberspace changes the landscape and boundaries of modern conflicts.
A digital attack can occur from anywhere in the world and can lay hidden for years until it’s issued the command to engage.
There have been a few high-profile examples of cyber-attacks from nation-states that caused extensive damage and even loss of life.
Here are just a few.
- Stuxnet (2010): As one of the most advanced cyber-weapons ever created, it targeted Iranian nuclear refinement centrifuges, caused extensive physical damage and severely degraded the Iranian nuclear development program. It is allegedly attributed to the US and Israel.
- Attack on Sony Pictures (2014): In response to the release of the movie “The Interview” that poked fun at the North Korean leader Kim Jong-un, a North Korean hacking group targeted Sony Pictures.
- Cloud Hopper (2015+): Attributed to the Communist Chinese Party (CCP) hacking groups APT10, these attacks were targeted at managed-service providers (MSPs) to gain access to a broad range of commercial companies and research firms. Allegedly, the operation was in support of China’s economic and commercial espionage.
- NotPetya (2017): One of the most damaging cyber-attacks in history, Russia released the NotPetya cyber-weapon on Ukraine. It targeted Ukrainian power grids, energy companies, airports and banks. Approximately 80% of the targets were in Ukraine, but another 20% were spread across multiple western countries.
- Solarwinds Supply Chain (2020): Attributed to Russian intelligence agencies, the attack targeted Solarwinds and embedded malicious code into their software. This subsequently got pushed out as an update to tens of thousands of their customers including government, academic and commercial entities.
U.S. Cyber Command Created in 2003
In response to the growing threat from nation-state actors in the cyber domain, and the parallel arms race in cyber weapons, the US created the US Cyber Command in 2003.
Subsequently, multiple Joint Forces consisting of 133 cyber mission teams within the military branches were placed under the US Cyber Command.
These are often referred to collectively as the Cyber Mission Force or CMF.
Like any newly created military force, they required advanced equipment, training and operational support to be successful.
SealingTech is one of the private sector companies that are entrusted with taxpayer dollars to make sure the mission of the CMF succeeds. This is a responsibility that we take seriously.
SealingTech’s mission of advising and supporting the US military in cyberspace centers around three major areas:
- Equip, train and provide operational support to the CMF
- Develop hardened systems that protect the most critical systems and data
- Rapidly modernize the DOD’s networks with innovative, new and increasingly more secure systems
Call to Action
SealingTech understands the importance of ensuring US is not vulnerable to external threats within the cyber domain.
We understand that it is the military’s role to defend our country from attacks in this domain, and it’s SealingTech’s mission to use our expertise to ensure they have what they need to be successful.
Military historians agree that one of the largest factors in the Allies’ winning WWII was the overwhelming contribution of the United Stated defense industrial base (commonly referred to as the DIB) to outproduce the rest of the world.
It was the ability for commercial companies to produce and provide advanced equipment and support to the troops on the ground that ultimately led to the victory of the Allies. That concept hasn’t changed in the cyber domain.
As a federal contractor, SealingTech is part of this Defense Industrial Base, and we play a critical role in providing cyber capabilities, training, and solutions to the DoD.
As a company, we are driven by our mission and are proud of the role we play in supporting our cyber warfighters along with those of our allies.
While the warfighters, our end customers, are on the front lines defending our freedoms, we provide them with the hardware, software and technology that ensures the success of their mission.
We have a symbiotic relationship to help, support and advance each other’s missions.
For 10 years, it has worked and worked well.
And with such a sound foundation, we plan to continue this successful cyber defense mission well into the future.
In the next post, we will address the SealingTech Business Model and Structure. This will be of particular interest to those trying to get into the cybersecurity business or profession.
If you have any questions about this post or our business, please contact marketing@sealingtech.com.
Related Articles
A Series of Fortunate Events – The Birth of Fly Away Kits: SealingTech from then to now
When SealingTech began as a cybersecurity company in 2012, we solely offered ‘technical engineering services.’ As one of our first contracts, we were working with the JRSS (Joint Regional Security…
The Importance of Compliance in Cybersecurity
More than ever, cybersecurity, as an industry and as a field, has been growing exponentially in terms of the workforce and reach. From commercial and conglomerate entities such as banks,…
DCO: Do You Know What Your Network Security Systems are Looking For?
Over the past 3 years, I have been supporting Defensive Cyber Operations (DCO) capabilities for various Department of Defense (DoD) customers, along with an additional 7 years within Network Security…
Sign Up for Our Newsletter
Get all the recent SealingTech news and updates right to your inbox!
Expect the best cybersecurity ebooks, case studies and guides - all in one place, once a month. Connect with us today!